Difference between revisions of "WRT54GL Linksys Routers"
| Line 72: | Line 72: | ||
=== Configuring multiple DHCP ranges === | === Configuring multiple DHCP ranges === | ||
| − | The instructions linked above suggest adding only the second range under services>Additional DNSMasq Options, however we ran into trouble when the number of connected clients got too large. | + | The instructions linked above suggest adding only the second range under services>Additional DNSMasq Options, however we ran into trouble when the number of connected clients got too large. The primary range as configured under setup>network setup uses the maximum number of clients to define the end of the range. This is a problem because your total maximum clients may be much larger when you combine multiple ranges or use subnets larger than /24. In order to work around this issue we did the following: |
# Disable DHCP under setup>network | # Disable DHCP under setup>network | ||
| − | # Add statements to services>Additional DNSMasq Options to configure all of | + | # Add statements to services>Additional DNSMasq Options to configure all of the DHCP ranges, including the primary one and the maximum number of clients. |
<pre> | <pre> | ||
dhcp-leasefile=/tmp/dnsmasq.leases | dhcp-leasefile=/tmp/dnsmasq.leases | ||
| Line 87: | Line 87: | ||
</pre> | </pre> | ||
| − | You can check your work by viewing the config file on the router via ssh at /tmp/dnsmasq.conf | + | You can check your work by viewing the config file on the router via ssh at /tmp/dnsmasq.conf before and after making the change. |
| + | |||
| + | One side effect of doing this is that you lose the ability to view DHCP status via the web interface. As a workaround you can view the leases at /tmp/dnsmasq.leases via ssh. | ||
Revision as of 13:31, 26 November 2012
Introduction
Things I have done with a WRT54GL router running ddwrt custom firmware:
- Single router with 2 subnets each with seperate vlan, IP block, DHCP server, and firewall rules.
- VLAN trunking
- QoS traffic prioritization based on IP address
- WPA encrypted wireless point to multipoint bridging
Things I may implement in the future:
- Multiple wireless networks on the same router with different SSIDs and different vlan tags
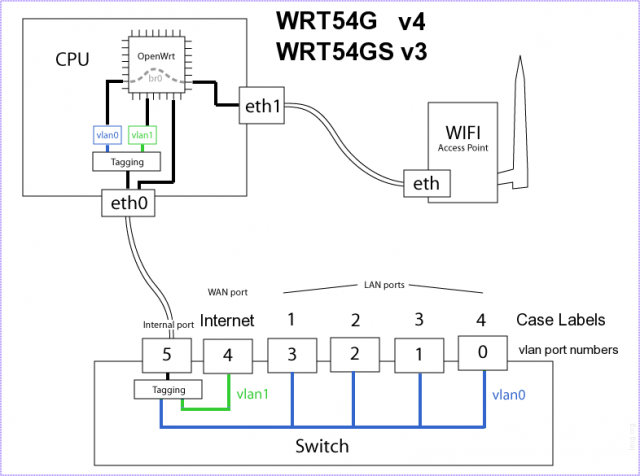
WRT54GL port diagram
Useful Links
WRT54GL ports in a table
http://nuwiki.openwrt.org/toh/linksys/wrt54gl#switch.ports.for.vlans
802.1q trunking instructions
http://www.geek-pages.com/articles/latest/802.1q_trunking_on_the_linksys_wrt54g/s/l_with_dd-wrt.html
Additional DNSmasq notes (for setting default gateway, etc)
http://www.dd-wrt.com/wiki/index.php/DNSMasq_as_DHCP_server
http://osdir.com/ml/network.dns.dnsmasq.general/2005-08/msg00046.html
Details
Configure an AP running DDWRT to do trunking
These steps assume you want to split out the wireless and the wired ports. Wired will be on vlan2 and wireless will be on vlan3 with both vlans trunked via the WAN port to a vlan aware switch. This router already has DHCP disabled and is not acting as a firewall, only an AP.
nvram set vlan0ports= nvram set vlan2ports="0 1 2 3 4t" nvram set vlan3ports="4t 5t" nvram set vlan3hwname=et0 nvram commit reboot
The last step is to configure your vlans in the web interface as follows:
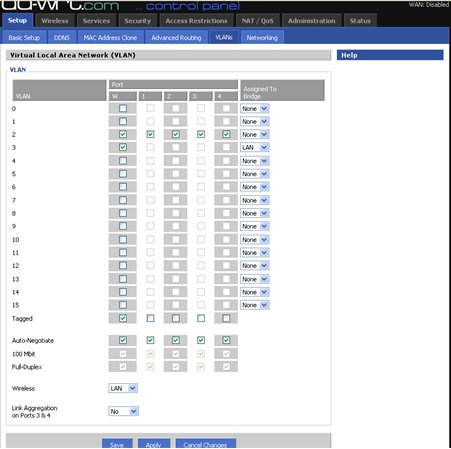
The end result is that you can use the same router to connect wired and wireless devices while keeping them on separate vlans.
Adding a third vlan and network
These steps assume you already have two other vlans configured and you only want to trunk the new vlan up to another switch. Also, there are additional steps required if you wanted to enable DHCP service on the new network.
Add ports to the new vlan
nvram set vlan4ports="0t 5t" nvram commit
Create a startup script to load firewall rules and configure the interface
echo '
#!/bin/ash
PATH="/sbin:/usr/sbin:/bin:/usr/bin:${PATH}"
iptables -I FORWARD -i br0 -o vlan4 -j ACCEPT
iptables -I FORWARD -i vlan4 -o br0 -j ACCEPT
iptables -I FORWARD -i vlan4 -o vlan1 -j ACCEPT
iptables -I INPUT -i vlan4 -j ACCEPT
ip addr add x.x.x.x/yy brd + dev vlan4
ifconfig vlan4 up
' > /jffs/etc/config/vlan4.startup
chmod 750 /jffs/etc/config/vlan4.startup
x.x.x.x/yy is the IP and mask you want to assign to the router on the new vlan.
Add the new vlan to the trunk port
In the web based DDWRT GUI add the additional vlan to your trunk port.
Configuring multiple DHCP ranges
The instructions linked above suggest adding only the second range under services>Additional DNSMasq Options, however we ran into trouble when the number of connected clients got too large. The primary range as configured under setup>network setup uses the maximum number of clients to define the end of the range. This is a problem because your total maximum clients may be much larger when you combine multiple ranges or use subnets larger than /24. In order to work around this issue we did the following:
- Disable DHCP under setup>network
- Add statements to services>Additional DNSMasq Options to configure all of the DHCP ranges, including the primary one and the maximum number of clients.
dhcp-leasefile=/tmp/dnsmasq.leases dhcp-lease-max=301 dhcp-option=3,192.168.1.1 dhcp-authoritative dhcp-range=192.168.1.101,192.168.1.200,255.255.255.0,1440m interface=vlan3 dhcp-range=wifi,192.168.2.50,192.168.2.250,255.255.255.0,60m dhcp-option=wifi,3,192.168.2.1
You can check your work by viewing the config file on the router via ssh at /tmp/dnsmasq.conf before and after making the change.
One side effect of doing this is that you lose the ability to view DHCP status via the web interface. As a workaround you can view the leases at /tmp/dnsmasq.leases via ssh.